
Scanner is a generic heuristic 68k virus scanner. It makes no assumptions about specific viruses, rather, it examines all the 68k resources (depending on the options set) in a file, looking for suspicious system calls. As such, it can be useful in determining in advance whether many resources (executable or not) try to alter other resources without the user's permission. Scanner is not meant to be a replacement for a professional Anti-Virus program, such as Virex or Norton Anti Virus for Macintosh. However, it can be useful as a prevention tool, prior to a detailed examination of suspicious files by professional Anti-Virus programs.
Scanner is NOT meant for novice users. It is recommended mainly for users who have adequate knowledge of some elementary Macintosh programming, or otherwise users who have a fairly good idea of how the Macintosh system calls and/or viruses work. If you find yourself not knowing what a Macintosh system call (trap) is, then this program will probably be more confusing to you than useful (Read the section below anyway). The reason being, that conventional Anti-Virus program scanners, store internally virus-pattern-strings and as such make their identification with 100% accuracy (well, almost...) and leave the end user free of the hassle of knowing how they work.
Scanner makes absolutely no assumptions about specific viruses, and depends on the process of heuristics to try to identify files as suspicious. The process of heuristics is based mainly on drawing probabilistic conclusions based on specific logical assumptions which can be made overall based on common viral behavior. While this behavior is largely predictable, there are always tricks a virus writer can use to avoid falling in the general category that Scanner assumes the virus is in, as such, the heuristics in the case of Scanner cannot be said to be absolute, rather probabilistic and non-deterministic. Non-deterministic does not of course mean that Scanner will fail, rather, that the results depend heavily on various assumptions, and even if these assumptions are correct, there is always room for error (in this case false positives and/or false negatives). Probabilistic in this sense, means that assuming that a virus belongs to a certain code category and uses common techniques to infect, then Scanner will raise specific flags, that is, it will signal the identification of suspicious code, with a probability of those code instances being viral depending on the previous assumptions, PLUS on specific search criteria which can be controlled through the program's options, PLUS on other wild factors, such as the context within which the actual code is executed in. For example, most extensions, use a certain system call to load themselves in memory and disassociate from the corresponding file from which they come. Many viruses also use this technique, to stay resident in memory after the infected file has been closed. As such, you can clearly see in this case for example, that what is a legal system call in one case, is illegal in another, depending on the specific context of whether the file is a valid extension or not.
The previous example is rather naive. There are many calls that viruses use, and determining whether such a call is legitimate or not, is a rather difficult task, if not impossible, because the context of execution cannot be known in advance, externally, unless the viral code executes in real-time. Advanced heuristics sometimes use emulation (the process of simulating pseudo-execution of a program's code without actually executing it through the machine's processor. Emulation heuristics are severely complicated and time consuming to the point of prohibition most times. (Many problems raise their ugly head upon emulating code, and the most severe is the halting problem). Although partial emulation heuristics have been implemented on PCs, on the macintosh the level of virus sophistication is not yet so high as to require emulation in order for Anti-Virus programs to identify viruses reliably. No doubt this will be needed one day, but as of now, one can use non-emulation heuristics, that perform specific code-target analyses in specific places, diminishing the time required thus, to practical levels.
Scanner does precisely such a heuristic analysis. It looks for suspicious system calls in 68k code, and then performs an analysis around those places, by either backtracking through the supposedly offending code, or simply picking up certain parameters which are likely to indicate trouble. Then, when the process has been completed, it signals its results to the user, who is left to his/her discretion as to what to do with them. My suggestion to you as a relatively novice user who wants to try the program out anyway, is to run the program first, and read the enclosed 'Help...' information. If, after reading the entire help section and this readme file it all sounds like Greek to you, then Scanner will most likely confuse you. Do not use it. If however, you feel like you understand the basic concepts of how Scanner works, feel free to use it as a COMPANION Anti-Virus scanner to your regular professional software. Scanner is NOT meant to be a replacement for such software. On the other hand, as the heuristic analyses that Scanner performs on 68k code are quite general, it will likely identify as suspicious new and unknown viruses, which you can later send for examination to a commercial Anti-Virus company, particularly if you experience suspicious behavior from my other companion INITs, Tracker and DelProtect.
Samples:
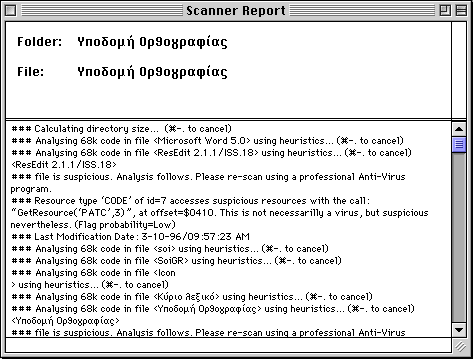
I had originally included a sample small directory with viral segment excerpts along with Scanner so you could see how Scanner performed on actual viral code. The actual code contained therein, was neither functional as a standalone virus of course, nor could you use it to reconstruct the actual viruses, because even if you disassembled it, it was only part of the actual virus. (I had simply cut/pasted resource segments from some common 68k viruses and have created new resource files where I put those segments in.) Upon more careful consideration though, and after the kind suggestion of Mrs Susan Lesch of Mac Virus, I decided to remove those samples from the download, to conform with standard Anti-Virus practices of not distributing viral code of any sort (even benign). I hope this does not really bother anyone. (If you wish to view a sample report on Scanner operating on real viruses, click here)
Download Scanner 1.x.x here. (The updates 1.x.x are related to small internal fixes and correcting typos in the Help section. This link always points to the latest version. (Latest version is 1.1.2) See the enclosed README file for more info.)